SSH Key-Based Authentication
SSH public key authentication is the preferred and a more secure way to login to a Linux server. By using keys and disabling password authentication it mitigates brute force attacks on passwords as the private key is required in order to authenticate.
Firstly, create a SSH key pair using the ssh-keygen command. There are multiple options which can be used when creating the key pair. By default the command will create a rsa key and place the private and public key in ~/.ssh/. In this example a 521 bit ed25519 key is created.
ssh-keygen -t ed25519 -b 521After entering the command it will prompt for the location to save the key and also to enter a passphrase. The passphrase is not required, however, it is advised to set a very strong passphrase which would be difficult for anyone to guess.
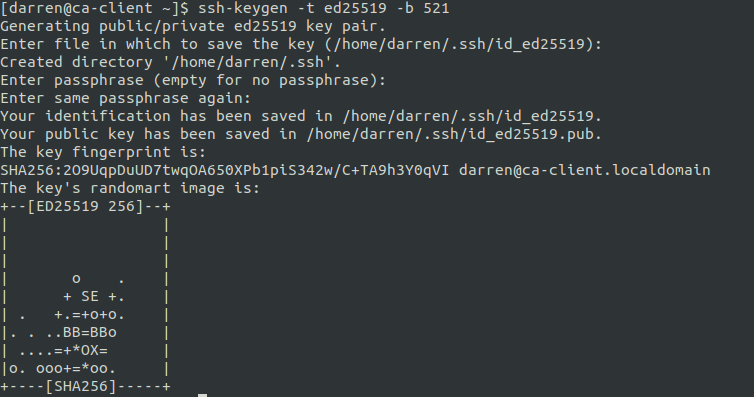
The command will complete and create a key pair. One part of the pair is the private key, as the name suggests this key needs to be kept private and should not be shared. The private key will be used when logging into servers. The second half of the pair is the public key this is the key which can be made public. This key copied onto remote servers to allow authentication using the private key.
The public key can simply be read using the cat command. The full output is what will need to be added on the remote server.
[darren@ca-client ~]$ cat .ssh/id_ed25519.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG893/Uj+01Q5uH27KI0jZhwf3DDBiDiUjT8b09L5ska [email protected]By default the authorized_keys file within openSSH is confgured in ~/.ssh/authorized_keys. This file is where the public key will be placed in order to authenticate with the private key.
If the directory does not already exist it needs to be created. Be careful to ensure appropriate permissions are applied on the directory and files. If additional access is set it will deny authentication when using the key.
mkdir ~/.ssh
chmod 700 ~/.ssh/
echo "ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIG893/Uj+01Q5uH27KI0jZhwf3DDBiDiUjT8b09L5ska [email protected]" >> ~/.ssh/authorized_keys
chmod 640 ~/.ssh/authorized_keys
When attempting to authenticate it will now prompt for the passphrase of the ssh key. Note, if the key name was saved to another location or with a different name the -i option will need to be supplied to state which key should be used.
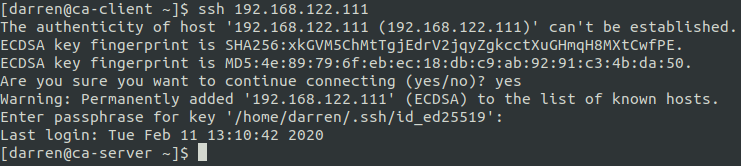
As ssh key authentication is now working as expected password authentication should be disabled. This can be completed by setting 'PasswordAuthentication no' in /etc/ssh/sshd_config and restarting the sshd service.
One further recommended configuration change to enhance the security of using ssh keys is to change the location of the authorized_keys file. The reason for this is by default any user can add public keys into their authorized_keys file. The security concern with this is users could ultimately provide access to their account to other users simply by adding other public keys. This could obviously prove to be a compliance issue and one which may ultimately lead to malicious behaviour.
To change the file location modify the AuthorizedKeysFile option within /etc/ssh/sshd_config. Ensure the new directory is only writable by root and the relevant user has read access to the file.
[root@ca-client auth_keys]# grep ^AuthorizedKeysFile /etc/ssh/sshd_config
AuthorizedKeysFile /etc/ssh/auth_keys/%u
[root@ca-client auth_keys]# ll /etc/ssh/auth_keys/
total 4
-rw-r--r--. 1 root root 584 Feb 11 20:13 darrenUsing Advanced Intrusion Detection Environment (AIDE) is an ideal tool to monitor for any changes in this directory.